Welcome Ziglets!!
Today’s Zigbit is going to be on Cisco Identity Services Engine, also known as ISE. That’s right its “ISE ISE baby” time!! For this session on ISE, we will be reviewing different use cases from some real world deployment examples. Names have been changed to protect the innocent.
Recently I was given the pleasure to present at a local Cisco Live event on Cisco ISE. I think some of the information I presented would be valuable for others that were not able to attend so I will share it here.
The different ways I am seeing customers utilize Cisco ISE today:
- Guest Access Management – Easily provide visitors secure guest Internet access
- BYOD and Enterprise Mobility – Seamlessly classify & securely onboard devices with the right levels of access
- Secure Access across the Entire Network – Streamline enterprise network access policy over wired, wireless, & VPN
- Network Device Administration – Device administration and Network Access on a single platform
- Visibility & Context Sharing with pxGrid – Share endpoint and user context to Cisco and 3rd party system
- Software-Defined Segmentation with Cisco TrustSec® – Simplify Network Segmentation and Enforcement to Contain Network Threats
Cisco ISE Use Case Architecture – High level
Cisco ISE Use Case Example: K – 12 School District
When I met with the customer they had some simple requirements:
- Full Visibility
- Secure Control
- Guest Access
- Ease of Management
Here is a quick summary of what we did to meet these customer requirements with Cisco ISE.
Full Visibility:
Implemented a Monitor Mode ISE Deployment. This allows the customer to implement a security policy but not block anything initially. Everything is tracked inside of ISE. This is where we get Full Visibility, or what I like to call the “Full Context Picture”, with the five Who, What, Where, When and How for each session on your network. I know this sounds salesy, that’s not the intent here I just like catchy phrases! Cisco ISE pulls all of this information together out of the box. You don’t actually have to configure any of the security policies initially; you could just have full visibility of your environment with very minimal work, which is totally an option.
In my experience, only 85 – 90% of the customer’s use cases are known at the time of the ISE deployment. The other 10 – 15% of the customer’s use cases are generally unknown by the IT department but are later discovered during the Monitor Mode window of 3 – 6 months. Once a use case is discovered, the creation of a new policy entry for the specific use case is easy to implement.
For this customer, they specifically had pain points with Gaming systems and Small Office Home Office routers so we restricted these devices from being connected to their network from day 1.
Secure Control:
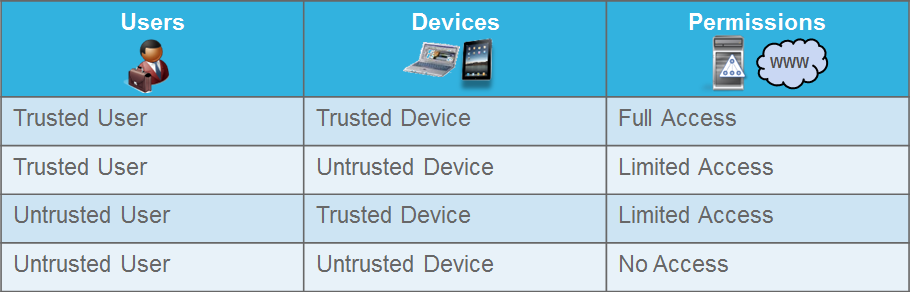
Following the High Level Architecture shown above, we implemented a Trusted / Trusted Security Architecture. Trusted devices were defined as anything that was procured and managed by the IT Department. With this definition, Trusted devices were pretty simple to identify within ISE.
For Trusted users, we had multiple tiers, or levels, with different access associated with each tier. For example, most K-12 School Districts have Employees and Students, both of which are Trusted users. In this case, users defined as Employees were given more access to the network and resources than users defined as Students. A step further for Employees for this customer, they had different access requirements for Staff and Faculty which we were able to associate directly through ISE and Active Directory.
Guest Access:
Ease of use by their user base was by far the most important business requirement for the customer. They wanted a single simple Guest portal. We deployed a self-sponsored guest access architecture were anyone could use guest but was limited to internet access and a small subset of printers in the customer’s DMZ. These self-sponsored guest accounts did not require any approval to be created but did expire after 8 hours of being active.
The second requirement from the customer was to implement an “IT Vendor” Sponsored Guest access but still utilizing the same Guest Portal as before. This second requirement allowed full access to the customer’s network but required the IT department to sponsor the guest accounts. These privileged guest accounts were configured to expire after two weeks of being active.
Ease of Management:
With this ISE deployment we were able to “migrate” all security configurations of the network to ISE, a single web portal front end. Let me remind everyone here that ISE is deployed in a cluster. This single web portal is not a single point of failure.
Before implementing ISE, this customer’s network consisted of the traditional static ACLs and static vlans on each switch for “X”specific reason(s). I’m sure most of you are all too familiar with this, dare I say it, legacy model. If you are not on that vlan or that subnet, you will not get the correct access you need. If you need to make a change to the ACL, you have to touch every Network Device. With the Downloadable ACL and VLAN override features in ISE, we were able to remove this legacy model. Now it didn’t matter what VLAN you were on, or what subnet you were on; your access was determined based on your Full Context Picture and the associated security policy implemented in ISE. From a management perspective you now only had to modify one ACL when making a change.
The final item to note is the reduced number of SSIDs from the wireless side of the house. The customer had 37 different SSIDs, around 3 SSIDs per school. We were able to reduce this number down to 2 SSIDs in total, an internal SSID and a guest SSID. Users would see the same SSIDs at every school, instead of having to connect to a different SSID at each school.
Summary:
As you can see we were able to solve all of the customer’s business requirements with Cisco ISE and give them a few additional benefits they were not even looking for. This is how I personally like to design a solution: Determine what the business requirements are first and then design or architect a solution that meets all of the customer’s needs, implicit and explicit! Sometimes the customers don’t even know what thier requirements are and those are the fun ones!
