Hey Ziglets, its ISE ISE Baby time!! Today we are continuing with our Cisco ISE 2.3 Blog Series by adding our NADs, or Network Access Devices, into our ISE Cluster. In our last episode we added our Cisco 3750e to our ISE Cluster. In this episode we are going to add our vWLC to our ISE Cluster. The vWLC Configuration is much more straightforward than the 3750e’s configuration. Lets jump right into it shall we?!?!?!
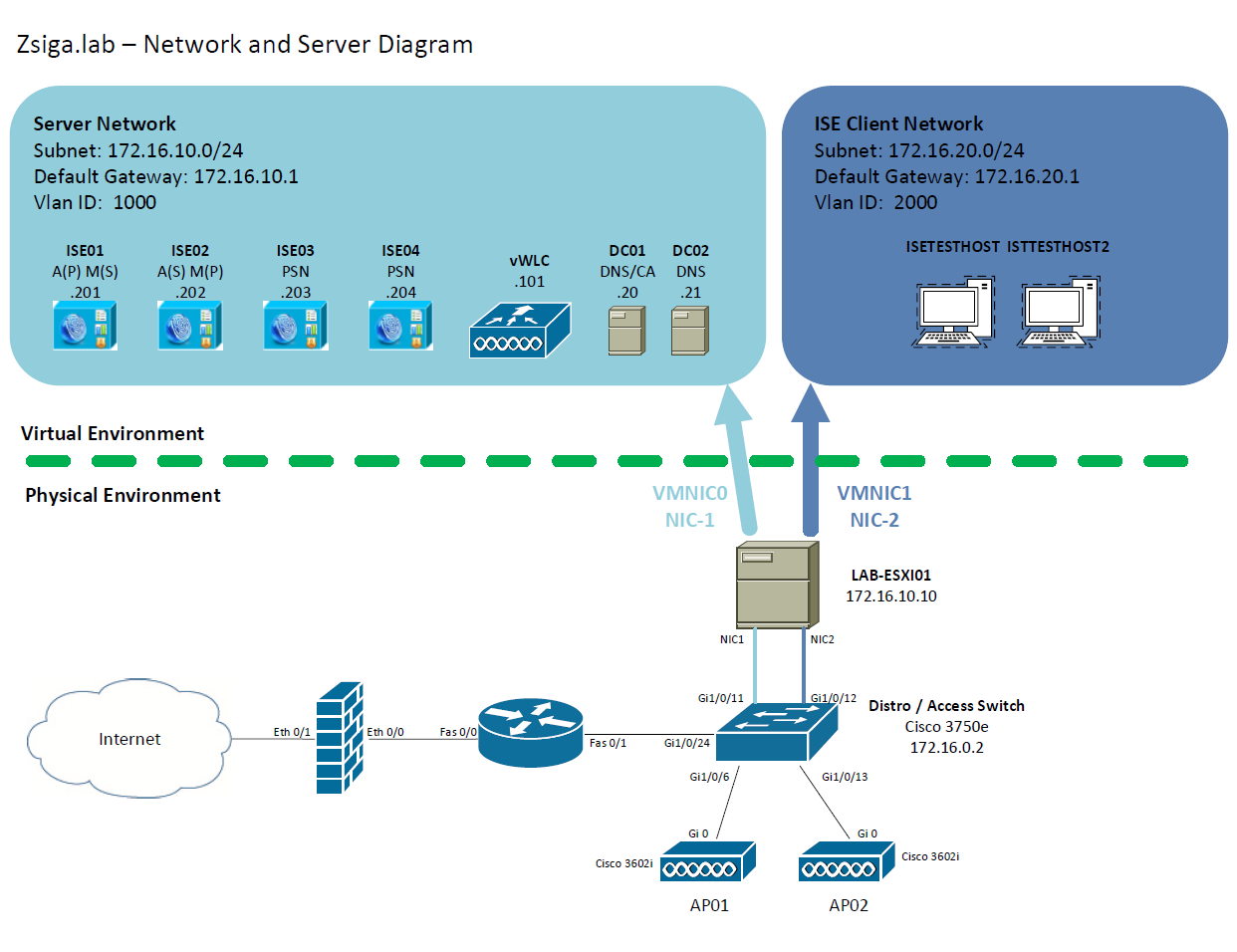
Network and Server Diagram:
Here is our reference diagram that we will be using throughout this blog series.
Related Posts:
If you haven’t seen these posts yet, you should check them out
- ZBISE01 – Basic Cisco ISE 2.3 VM Installation
- ZBISE02 – Building a Cisco ISE 2.3 Distributed Cluster
- ZBISE03 – Overview of our Cisco ISE 2.3 Use Cases for the ZBISE Blog Series
- ZBISE04 – Cisco ISE 2.3 Adding the ISE Cluster to Active Directory
- ZBISE05 – Virtual Wireless LAN Controller (vWLC) Install
- ZBISE06 – Cisco ISE 2.3 Adding Network Access Devices (NADs) – Cisco Switch
The Steps!!
We are going to add our lab’s Cisco Virtual Wireless LAN Controller (172.16.10.101), that we built in ZBISE05 – Virtual Wireless LAN Controller (vWLC) Install, as a Network Access Device, or NAD, into ISE. There are a number of configurations that will need to be added to both the vWLC and the ISE Cluster, but the vWLC is pretty straightforward compared to the Cisco 3750e switch we did in the previous episode, episode ZBISE06 – Cisco ISE 2.3 Adding Network Access Devices (NADs) – Cisco Switch.
1. The vWLC “Global” Configuration:
Launch a browser and enter in your vWLC’s IP address. In our case, we are using Chrome for our browser and our vWLC’s IP address is 172.16.10.101.
In most cases, you will get a Certificate Security warning because the vWLC is built with a Self Signed Certificate. Accept this warning and continue in what ever way it lets you.
Once you get to the login screen, enter the appropriate account information to log into your vWLC
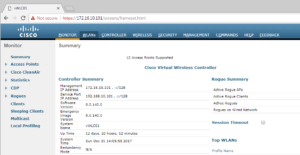
On first window we see once logged into the vWLC, we want to select the Security menu at the top, about the middle of the screen.
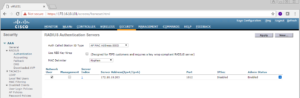
Now that we are in the Security Menu, we want to select AAA -> Radius -> Authentication on the left pane’s menu.
Here is where we are going to start to add our ISE Nodes into our vWLC, or NAD. We only need to add the ISE nodes that will be running the Policy Services persona for this vWLC. In our Lab deployment this is going to be ISE03 (172.16.10.203) and ISE04 (172.16.10.204).
Click the New… button near the top right of this window to start this process.
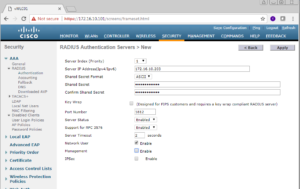
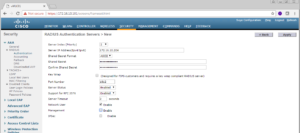
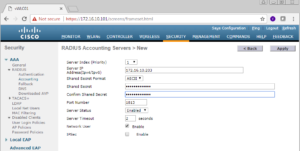
You should now see a screen similar to the below screenshot, without the information filled in ;).
Go ahead and fill in the information for your specific PSNs, for our case here we are going to add the IP addresses for both ISE03 and ISE04, 172.16.10.203 and 172.16.10.204 respectively. Our shared secret is going to be ZBISE_INSTALL and we are going to make sure “Support for RFC 3576” is enabled. Finally, I like to uncheck the Management checkbox as we are not using our ISE Cluster right now for Device Management, just for Network User Authentication.
Once satisfied, click the Apply button in the top right of the screen.
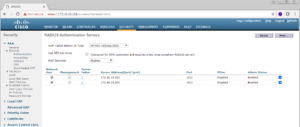
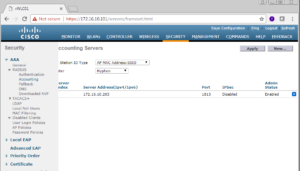
The next screen is the Authentication page again, now we have our first PSN in the table list in this window. You can repeat the same process to add more PSNs into your vWLC that can be used for Authentication. Included below are screenshots of us adding our second PSN, ISE04, to our vWLC for Authentication.
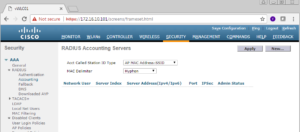
Now we are going to repeat this same process but for the Accounting subsection (Security -> AAA -> Radius -> Accounting).
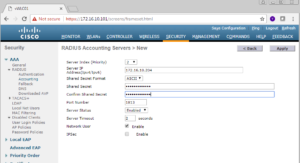
Once you actually select Accounting, you will see a similar screen as the Authentication page. In the top right there will be a New button that you will need to select to add your PSNs.
On the next screen, it is once again similar to the Radius Authentication Servers page. Here we are going to put our PSN IP Addresses (172.16.10.203 and 172.16.10.204) along with the shared secret ZBISE_INSTALL.
Once completed, click the Apply button in the top right of the window.
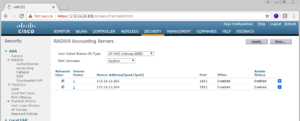
You should be brought back to the Radius Accounting Servers window, where you will now see your newly added PSN in the table list. Repeat this same process for all of your PSNs you plan to use on this vWLC. Below are screenshots showing us adding ISE04.
That’s it for the global configurations, lets now show you how to utilize these within an SSID.
2. The vWLC “SSID” Configuration Example:
We finished the Global changes, now lets show you an example SSID and how to utilize these Radius servers we have configured.
NOTE: This SSID is just an example, not all settings are configured. When we create the Lab SSIDs in a later installment we will show what settings we change for each SSID.
You should be logged into your vWLC via the Web front end, if you are not go ahead and get there now. I had logged out, so I just logged back into my vWLC.
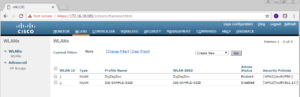
Click the WLAN menu item.
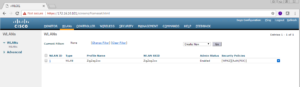
In the WLAN window, you will see a list of all of your SSIDs, in the below screenshot you see my ZigZagZoo SSID for example.
Lets go a head an create a new SSID. To do this, make sure Create New is selected in the drop down box near the right of the screen, then click the Go button.
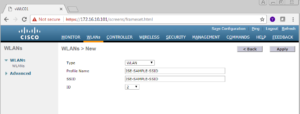
You will arrive on the WLAN -> New Page, where you will need to specific the SSID Type, Profile Name, SSID, and ID. For this example we did these settings: WLAN, ISE-SAMPLE-SSID, ISE-SAMPLE-SSID, 2 respectively. Once you have the information filled out how you want too, click the Apply button in the top right.
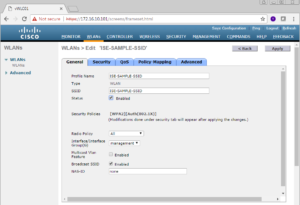
Now that you have started the configuration of the SSID, you will be directed to a full configuration window for this new SSID. That will look similar to the below screenshot. Here is where you can enable the SSID, select which interface for it to use, and a number of other settings.
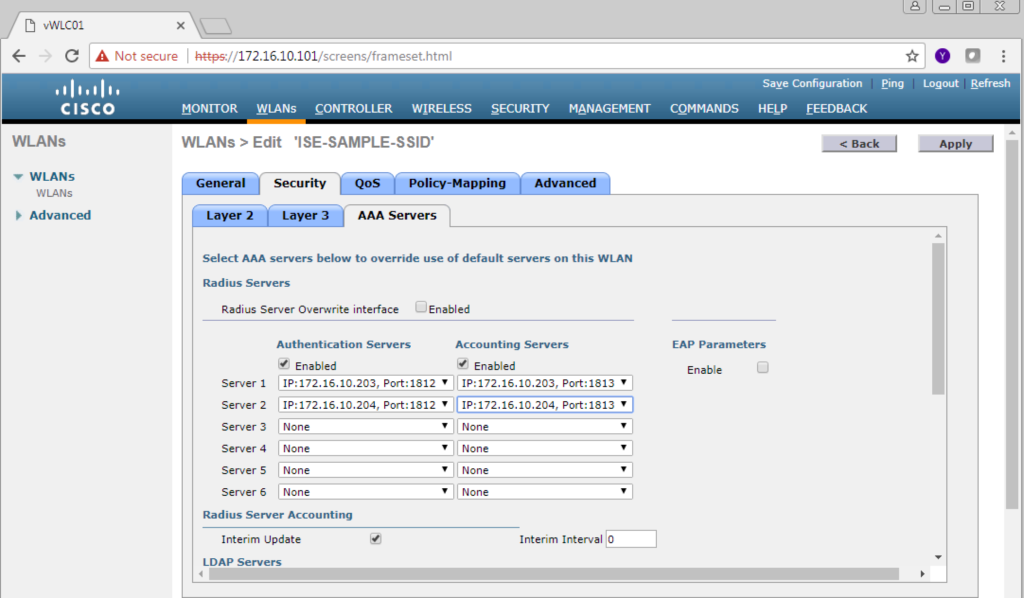
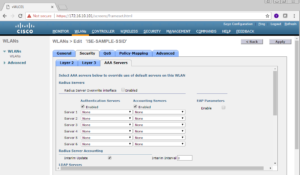
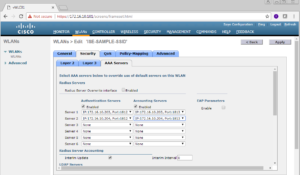
For this example we are really only concerned with the Security Settings. Go ahead a click Security then AAA Servers.
In this sub window, there are dropdown boxes that will allow us to select our PSNs we added in Step 1 above. Lets go ahead and select each PSN for both Authentication and Accounting. The screenshots below show that we have selected ISE03 and ISE04 respectively.
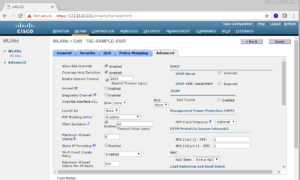
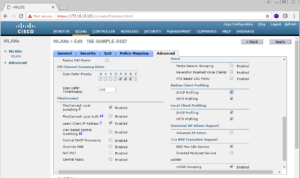
Once you have selected your AAA servers (Your PSNs), go a head and select the Advanced tab. On the Advanced tab we want to Allow AAA Override and enable Radius NAC. To Allow AAA Override, we just need to select the checkbox on the left top side of the screen where it says “Allow AAA Override”. To enable Radius NAC we need to find the NAC section on the right side of the screen and in the NAC State Dropdown box we want to select Radius NAC.
NOTE: There are other settings we may / may not change on this screen depending on how our ISE and Wireless Deployment is. We will go over them when we make those changes in another episode.
Below are screenshots showing the changes we stated above. Once all is good, click the Apply button…You guessed it, in the top right once again! 🙂
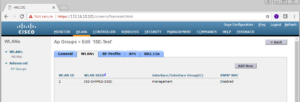
You will be redirected back to the WLANs Summary screen, that lists all of your SSIDs. Your SSID Configuration is completed at this stage, but if you are like me and have AP Groups configured, we will need to at our newly created SSID to a corresponding AP Group. You guessed it, we are going to show you how to do this below.
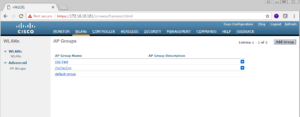
On the WLANs Screen, on the left side menu, expand the Advanced Sub level menu item and select AP Groups.
On the AP Groups screen that loads, you will see a list of all of your AP Groups. In our case we have three, ISE-Test, ZigZagZoo, and default-group.
Select your appropriate AP Group that you will be using for this deployment. In our Lab I am going to use our ISE-Test AP Group.
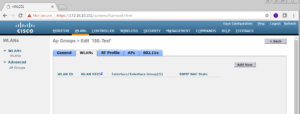
On the AP Groups edit page, select the WLANs Menu. On the right side of this screen, click the Add New button.
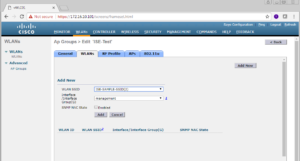
On this following page, you will need to select your SSID, in our case its ISE-SAMPLE-SSID. You will also need to select the Interface that the SSID will use. We selected the Management interface. Once ready, click the Add button.
Once added, you will be redirected back to the AP Groups Edit page and you should see your SSID in the table at the bottom of the window.
Thats it, we are now completed with our vWLC configuration for this episode. Great timing because I am getting Hangry!! 🙂
3. The ISE Cluster Configuration:
Before I run off and get some much needed subsistence, we need to add our vWLC into our ISE Cluster! Silly me!
Launch a browser to your ISE Admin Node. In our case, we used Chrome and browsed to https://ISE.zsiga.lab. When prompted to login, enter the appropriate credentials.
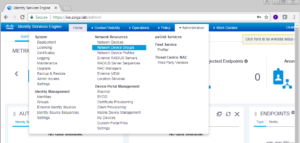
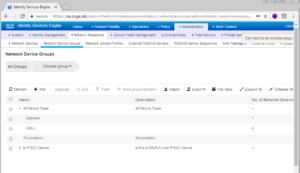
Once logged into your ISE Cluster, we need to first go to Network Device Groups, so we can create a vWLC group. Select Administration -> Network Resources -> Network Device Groups.
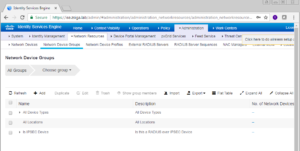
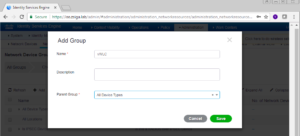
On this page, click the Add button to add a new Device Group
You will be presented the Add Group window where you can specific a name, a description, and a Parent Group for your group. In our case, we named our group vWLC with no description and no Parent Group.
Click Save when you are good to go.
The next window shows your newly created Device Group.
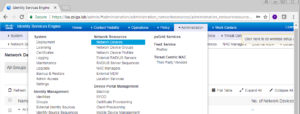
Now lets add our vWLC. Select Administration -> Network Resources -> Network Devices.
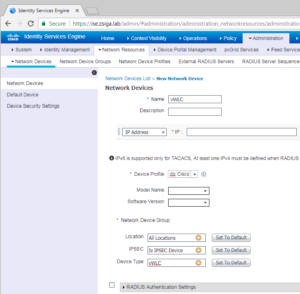
On the Network Devices page, click the Add button to start the process of adding our vWLC.
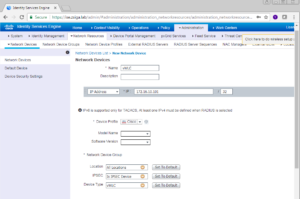
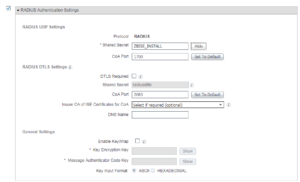
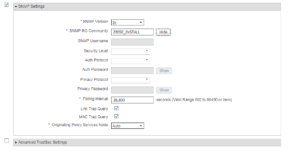
Finally, we now can add all of the information for our vWLC. Here we give it a name, the IP address and fully configure Radius and SNMP. Our Name is vWLC, the IP address is 172.16.10.101, and our Radius/SNMP string is ZBISE_INSTALL. Once you have everything configured for your vWLC click the Submit button at the bottom of the window. Below are all of the screenshots showing our configurations for our vWLC.
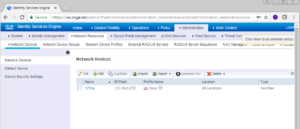
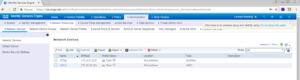
Once your vWLC has been added you will be brought back to the Network Devices page showing you all of the configured network devices.
Thats it!! We did it! We now have our vWLC configured for ISE and vice versa!!!!! We are one step closer to authenticating end devices and users with ISE.
Related Resources:
Ask questions and give feedback
- You can leave a comment on the blog!
- You can leave a voicemail at (617) 913-4103
- You can email us at Feedback@zigbits.tech
Engage with Zigbits further:
- Subscribe to the podcast on an iPhone or on an Android
- Follow Zigbits on Twitter!
- Follow Zigbits on LinkedIn!
- Follow Zigbits on Facebook!
Engage with me further:
Transparency:
This post may contain affiliate links to products or services were I may receive a level of compensation from your actions by following those links. This is seamless to you and does not add any additional cost to the products or services in question. In addition, I do not let any affiliate relationship cloud my judgement or my recommendation of a product or service. My recommendations will always be above reproach. This is my commitment to you Ziglets!

Great Post. Hope another ISE post.Thank.
Thanks Saw, Appreciate the comment! More ISE Posts to come soon! 🙂