Here is our Final Cisco ISE 2.3 Wired Use Case. Today we will implement our Cisco Access Point Policy which will utilize MAB Authentication and a Logical Profile to categorize the Cisco Access Point. Not much else to say but that, so lets get to it!
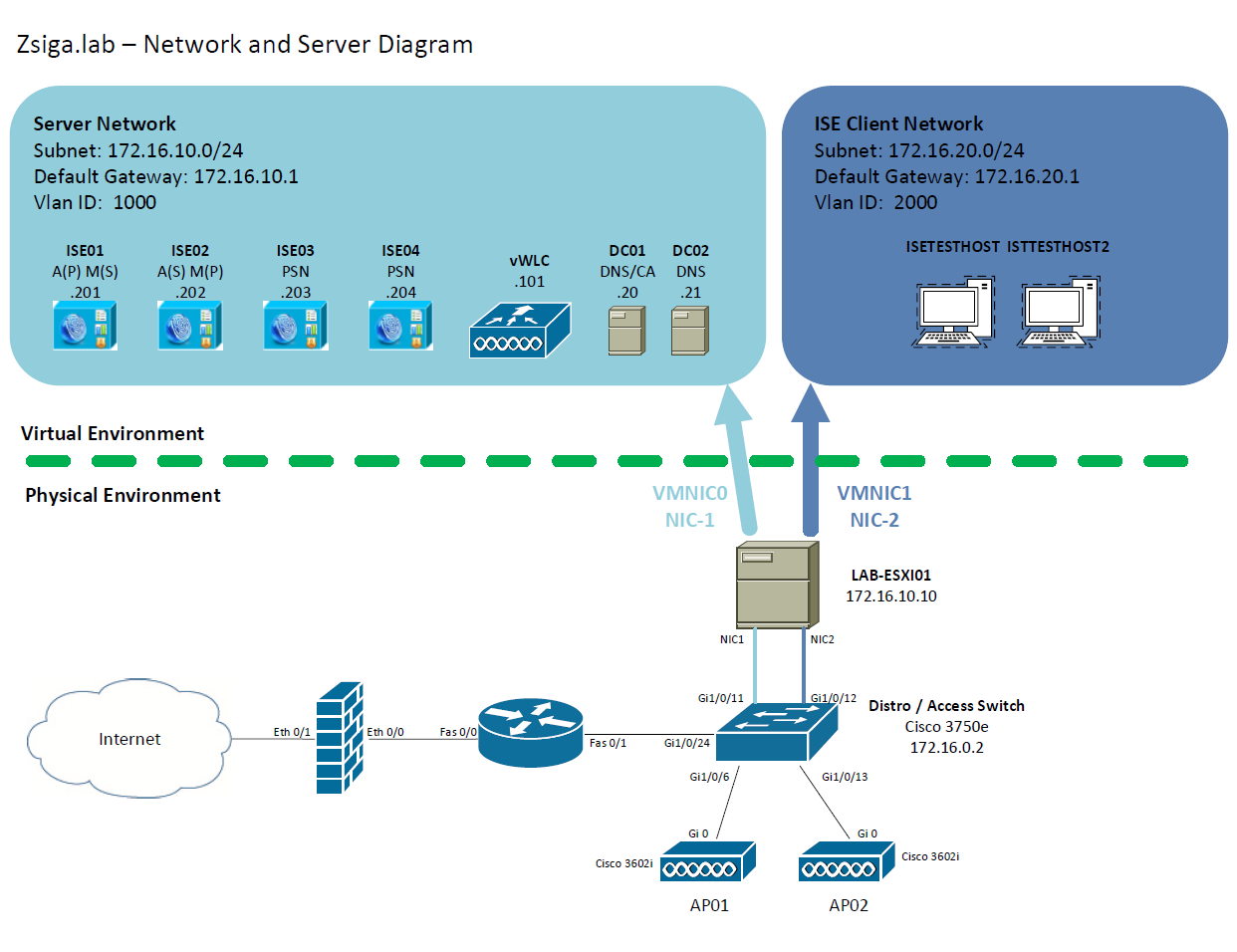
Network and Server Diagram:
Here is our reference diagram that we will be using throughout this blog series.
Related Posts:
If you haven’t seen these posts yet, you should check them out
- ZBISE01 – Basic Cisco ISE 2.3 VM Installation
- ZBISE02 – Building a Cisco ISE 2.3 Distributed Cluster
- ZBISE03 – Overview of our Cisco ISE 2.3 Use Cases for the ZBISE Blog Series
- ZBISE04 – Cisco ISE 2.3 Adding the ISE Cluster to Active Directory
- ZBISE05 – Virtual Wireless LAN Controller (vWLC) Install
- ZBISE06 – Cisco ISE 2.3 Adding Network Access Devices (NADs) – Cisco Switch
- ZBISE07 – Cisco ISE 2.3 Adding Network Access Devices (NADs) – Cisco vWLC
- ZBISE08 – Cisco ISE 2.3 Wired Authorization Profiles
- ZBISE09 – Cisco ISE 2.3 802.1x Auth – PEAP Wired Use Cases
- ZBISE10 – Cisco ISE 2.3 802.1x Auth – EAP-TLS Wired Use Cases
- ZBISE11 – Cisco ISE 2.3 Cisco VoIP Phone with MAB Auth on Wired
- ZBISE12 – Cisco ISE 2.3 Xbox One with MAB Auth on Wired
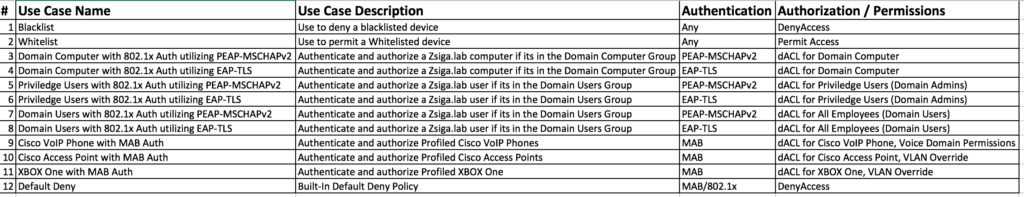
Wired Use Cases
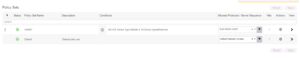
Here is our Wired Use Cases table for reference as we go through today’s installment of creating our Cisco Wireless Access Point with MAB Auth Use Case! This is our final Wired Use case for our deployment!!
The Steps!!
1. Create our ISE Policies for our Cisco Access Point Use Case
Lets jump into our ISE cluster and configure our Cisco Access Point Use Case elements. If you have been following our Blog Series, you should be able to use your ISE FQDN like ours in our lab: https://ise.zsiga.lab. Log in appropriate ISE Credentials.
Once logged into your ISE Cluster, traverse to your Wired Policy Set. Policy -> Policy Sets -> Wired.
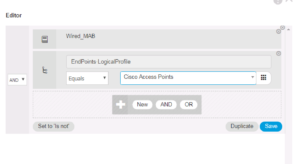
Once within your Wired Policy Set, duplicate the XBOX One Mab Authorization rule like shown in the below screenshot.
For the new Policy element, we named ours WIRED MAB Cisco Access Point, we selected the WIRED-ACCESS-POINT Authorization Profile and for the our condition information we selected Wired_MAB and the Logical Profile Cisco Access Points as shown in the below two screen shots.
Thats it for the ISE changes so lets save them and move on too Step 2! 🙂
2. Configure our Switchport for ISE…ISE THAT PORT…ISE THAT PORT!!
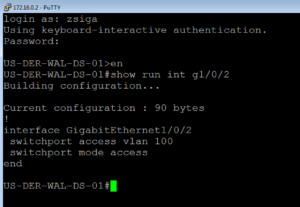
Lets check our Cisco Access Point port of Gi1/0/2. As we see below, its configured as an access port and is assigned for VLAN 100.
Taking a look at our port, we can see that it has not been ISED yet! Well lets go ahead and ISE that Port!!
It is time to ISE THAT PORT!
Lets pull the ISE Port Configuration from ZBISE06.
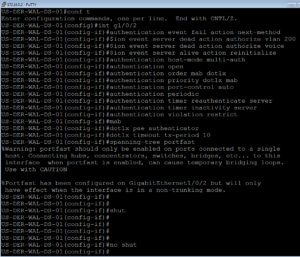
Below is what we are going to use for our ISE Port Configuration.
switchport access vlan 200 switchport mode access authentication event fail action next-method authentication event server dead action authorize vlan 200 authentication event server dead action authorize voice authentication event server alive action reinitialize authentication host-mode multi-auth authentication open authentication order mab dot1x authentication priority dot1x mab authentication port-control auto authentication periodic authentication timer reauthenticate server authentication timer inactivity server authentication violation restrict mab dot1x pae authenticator dot1x timeout tx-period 10 spanning-tree portfast
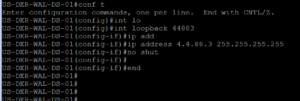
Below, like usual, is a screenshot of our switchport after the ISE Port configuration has been applied.
Now lets move into Step # 3!!
3. Validation and Testing of our Cisco Access Point Use Case
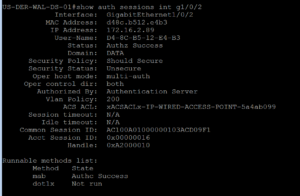
On our Lab switch, lets pull out our favorite CLI command, show auth sessions, to see what is taking place with our port.
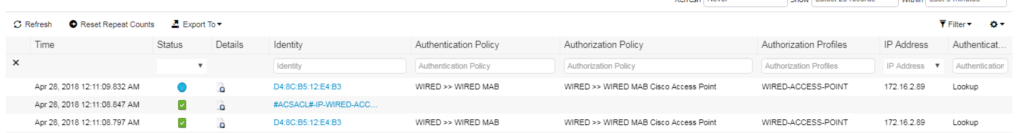
As we expected to see, our Cisco Access Point is getting a successful AuthC and AuthZ.
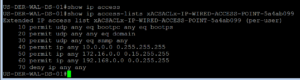
If we take a quick look at the dACL just to verify its correct, it should be but we never know. 😉
And look at that, the dACL is correct.
Lets jump over to the ISE Radius Live log side, to view what ISE shows for the authentication session.
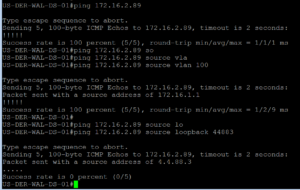
Now we just need to verify the dACL is properly working as expected. We should be able to ping the Cisco Access Point from an internal IP address (RFC 1918) but we shouldn’t be able to ping it from a public address. Lets add a new “public” address in our lab other than 1.1.1.1. For now we will use my CCIE Number, because I am a nerd and it just made sense, 44883. The IP Address will be 4.4.88.3!!
Below is the screenshot of our testing, and it looks like everything is working as expected!! We are good to go!
The dACL applied is working as expected.
Lets check to see if our Cisco Access Point has registered with our Virtual Wireless LAN Controller and if its in the proper Access Point Group. Our Virtual Wireless LAN Controller is 172.16.10.101.
Browse to https://172.16.10.101, you will get a screen similar to the below screenshot.
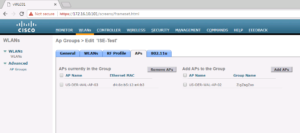
Once logged into the Virtual Wireless LAN Controller, traverse to WLANs -> Advanced -> AP Groups.
Within our AP Groups, we have an ISE Test AP Group, lets select that.
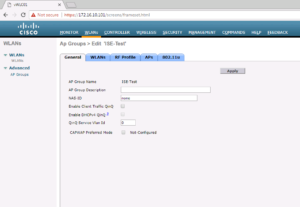
Once inside the ISE Test AP, select the AP Tab.
On the AP tab, we can see this AP is correctly associated with our ISE Test AP Group.
And that is it for our Cisco Access Point MAB Auth use case and the last of our Wired Use Cases. Our Next installment of this Cisco ISE Blog Series will be focusing on our Wireless Use Cases! I can’t wait, can you?!?!?! 🙂 As always, if you have any issues or questions, leave a comment and I will be there to assist!!
Related Resources:
Ask questions and give feedback
- You can leave a comment on the blog!
- You can leave a voicemail at (617) 913-4103
- You can email us at Feedback@zigbits.tech
Engage with Zigbits further:
- Subscribe to the podcast on an iPhone or on an Android
- Follow Zigbits on Twitter!
- Follow Zigbits on LinkedIn!
- Follow Zigbits on Facebook!
Engage with me further:
Transparency:
This post may contain affiliate links to products or services were I may receive a level of compensation from your actions by following those links. This is seamless to you and does not add any additional cost to the products or services in question. In addition, I do not let any affiliate relationship cloud my judgement or my recommendation of a product or service. My recommendations will always be above reproach. This is my commitment to you Ziglets!