I know its been a long time in waiting for this next Cisco ISE 2.3 Blog Series Post, well here it is!! Today’s post is going to cover our Cisco ISE 2.3 Wireless Authorization Profiles for our Wireless (WLAN) use cases. These are the permissions we are going to give authenticated devices / users!!
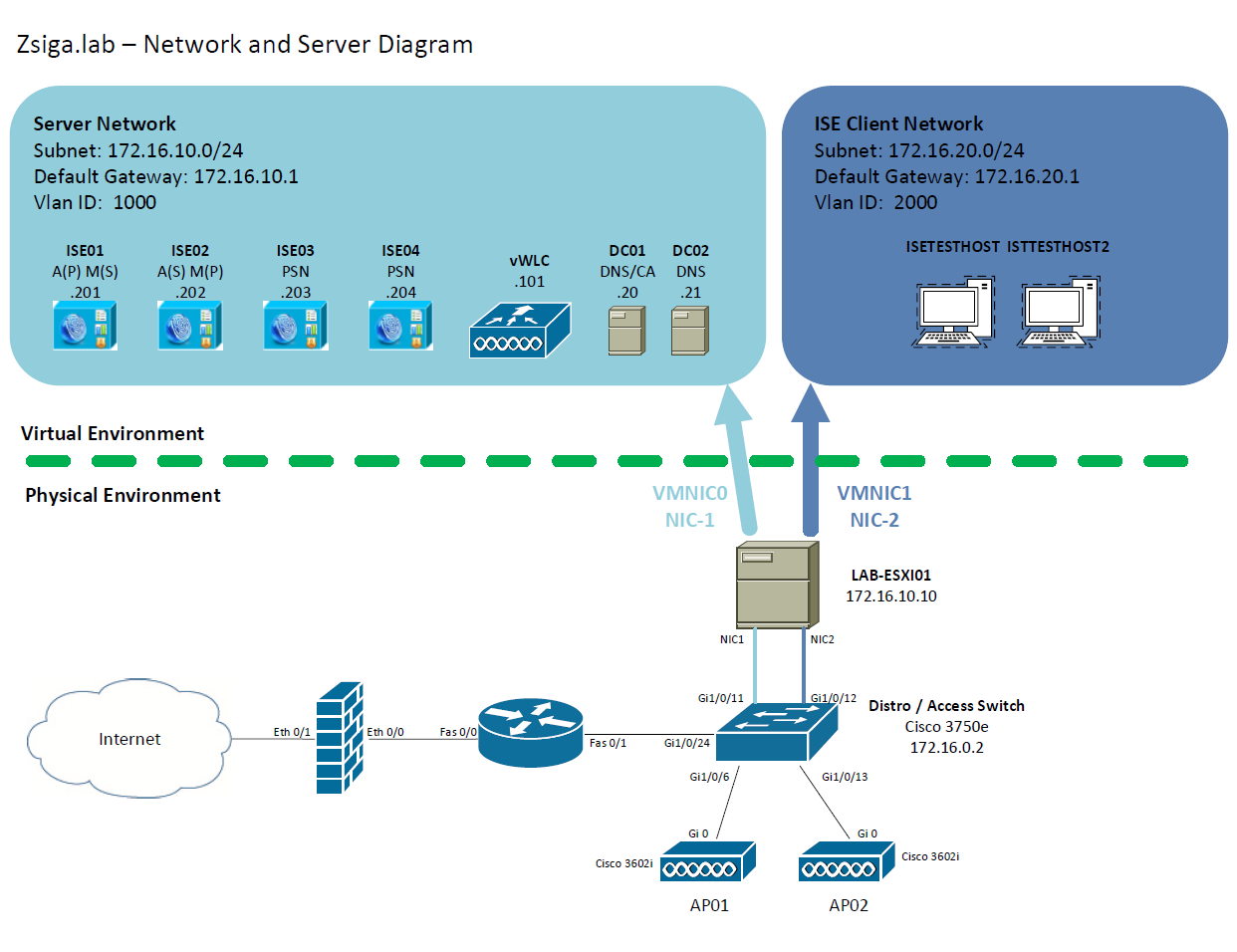
Network and Server Diagram:
Here is our reference diagram that we will be using throughout this blog series.
Related Posts:
If you haven’t seen these posts yet, you should check them out
- ZBISE15 – Cisco ISE Wireless Authorization Profiles
- ZBISE14 – Cisco ISE Creating WLC ACLs on Your vWLC
- ZBISE13 – Cisco ISE Cisco Access Point with MAB Auth on Wired
- ZBISE12 – Cisco ISE XBOX One with MAB Auth on Wired
- ZBISE11 – Cisco ISE Cisco VoIP Phone with MAB Auth on Wired
- Cisco ISE EAP-TLS 802.1x Auth – EAP-TLS Wired Use Cases – ZBISE10
- ZBISE09 – Cisco ISE 802.1x Auth – PEAP Wired Use Cases
- ZBISE08 – Cisco ISE Wired Authorization Profiles
- ZBISE07 – Cisco ISE Adding Network Access Devices (NADs) – Cisco vWLC
- ZBISE06 – Cisco ISE Adding Network Access Devices (NADs) – Cisco Switch
- ZBISE05 – Virtual Wireless LAN Controller (vWLC) Install
- ZBISE04 – Cisco ISE Adding the ISE Cluster to Active Directory
- ZBISE03 – Overview of our Cisco ISE Use Cases for the ZBISE Blog Series
- ZBISE02 – Building a Cisco ISE Distributed Cluster
- ZBISE01 – Basic Cisco ISE VM Installation
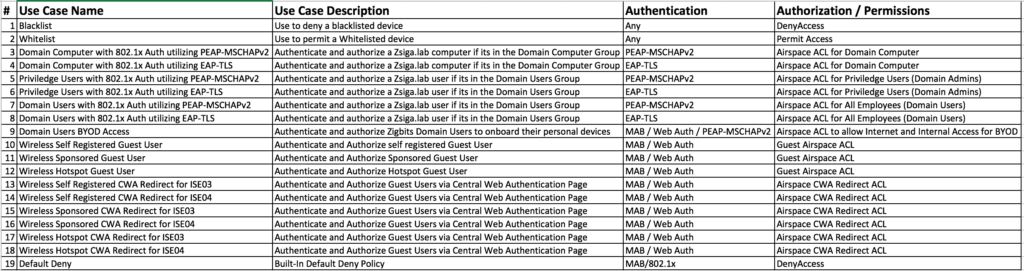
WLAN Use Cases
Here is our Wireless Use Cases table for reference as we go through today’s installment.
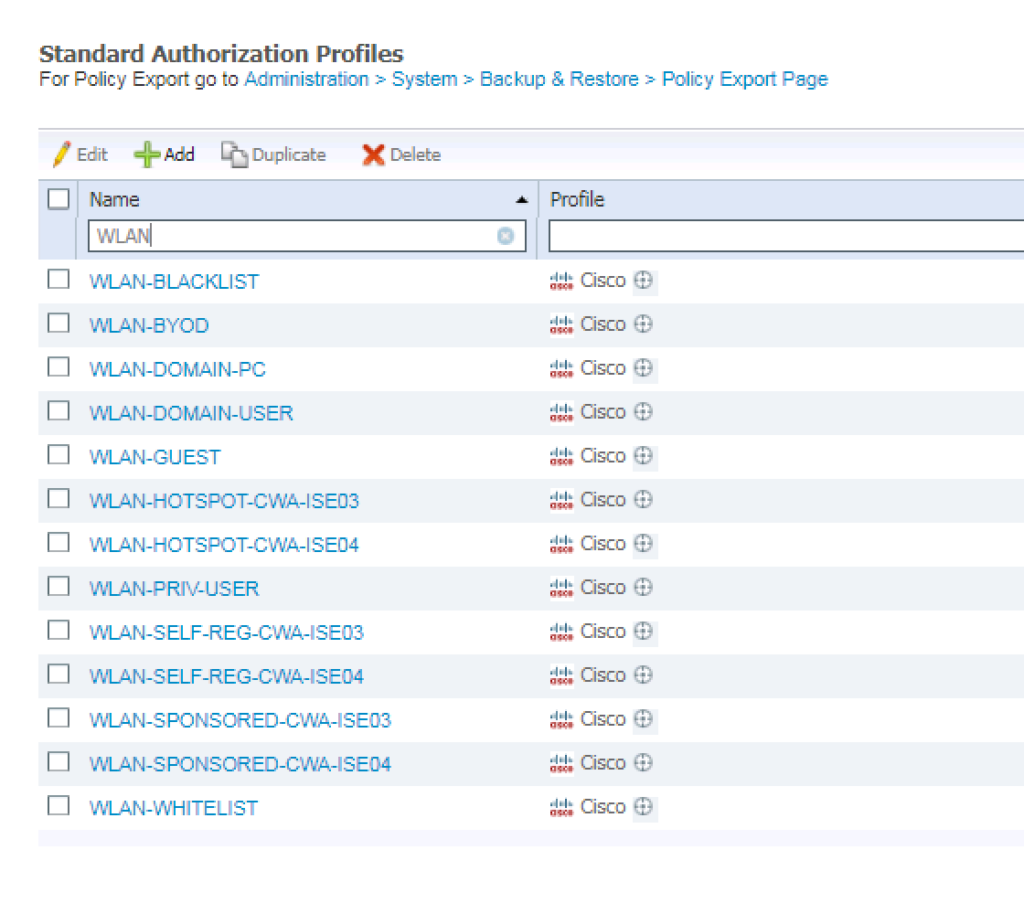
WLAN Authorization Profiles
Here is a list of the WLAN Authorization profiles we are going to create in today’s installment of the ZBISE Blog Series.
Note: For this deployment example, we are really only using a couple of the Authorization Profile options that we have at our disposal, you could easily do a number of other options if your design required it. For example, you can set the QoS levels for the specific session. The list of options is pretty log to go through and we will only be touching a small percentage of them.
- WLAN-BLACKLIST
- WLAN-WHITELIST
- WLAN-DOMAIN-PC
- WLAN-PRIV-USER
- WLAN-DOMAIN-USER
- WLAN-BYOD
- WLAN-GUEST
- WLAN-SELF-REG-CWA-ISE03
- WLAN-SELF-REG-CWA-ISE04
- WLAN-SPONSORED-CWA-ISE03
- WLAN-SPONSORED-CWA-ISE04
- WLAN-HOTSPOT-CWA-ISE03
- WLAN-HOTSPOT-CWA-ISE04
Lets get started!!
The Steps!!
Each of our ZBISE Blog Series Installments Builds on the previous one and this is the same here. In this installment we will be referencing the WLC ACLs we created in our last post, ZBISE14, so I highly recommend taking a look at it and seeing how the Zigbits WLC ACL Creator can help you!
As is usual, we first need to log into our ISE Cluster. Launch your Browser and lets get into it.
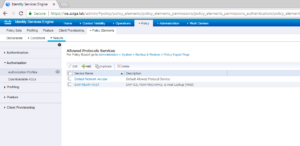
Once logged into your ISE Cluster, traverse to Policy -> Policy Elements -> Results.
At the Results screen, on the left pane select Authorization – > Authorization Profiles.
Here on the Authorization Profiles page, you will see all of the Wired Authorization Profiles we created back in ZBISE08 – Cisco ISE 2.3 Wired Authorization Profiles
1. WLAN-BLACKLIST
To create a new Authorization Profile, click the Add option on the Authorization Profile window. You will be taken a screen that looks similar to the below screenshot. This will be the same process for each Authorization Profile you create within ISE. For each Authorization Profile I took two screenshots, the configuration portion of the Authorization Profile and the Radius Attribute Portion of the Authorization Profile so you can see how it looks both ways.
The First WLAN Auth Profile we are creating is our WLAN-BLACKLIST which is just going to reject access all together.
Here is the Wireless Authorization Profile Configurations:
Here is the Wireless Authorization Profile Radius Attributes:
2. WLAN-WHITELIST
The Second WLAN Authorization Profile is very similiar to the first one, its called WLAN-WHITELIST, but instead of Rejecting Access we are going to use the Radius Permit Access to allow the authenticated session.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
3. WLAN-DOMAIN-PC
Now here is where we start to get a little more “complicated”, its not really complicated its all really easy, we are just selecting more configuration options based on what we are trying to do. For this use case we are going to use Access Accept and then we are going to call an Airespace ACL with the Name WLAN-DOMAIN-PC, which if you recall from ZBISE14 this is the WLC ACL we created for this use case. Thats it for this one! Take a look at the screenshots below to see how we did the ISE Specific Configurations!
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
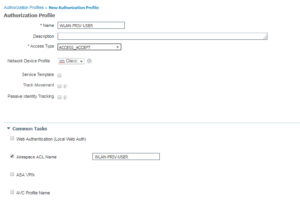
4. WLAN-PRIV-USER
This one is similar to the last one, we are just going to call a different Airespace ACL named WLAN-PRIV-USER. If you have any questions regarding these Airespace ACLs you can check them out in the last blog post, ZBISE14.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profile Radius Attributes:
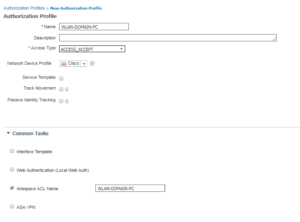
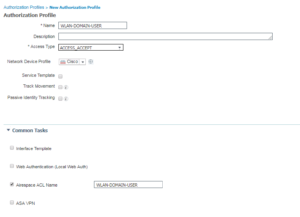
5. WLAN-DOMAIN-USER
And once again, this one is also similar to the last three Authorization Profiles. We do the Access Accept and we are calling an Airespace ACL but this one is named WLAN-DOMAIN-USER.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
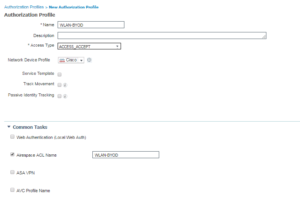
6. WLAN-BYOD
Same thing here, we are just calling a different Airespace ACL, in this case its WLAN-BYOD.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
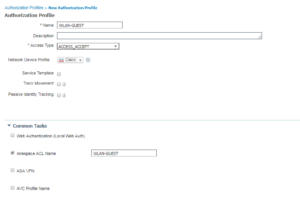
7. WLAN-GUEST
And finally one last similar Authorization Profile where we call the WLAN-GUEST Airespace ACL.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
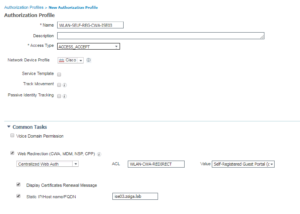
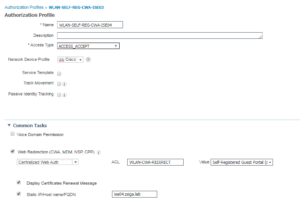
8. WLAN-SELF-REG-CWA-ISE03
Now here is where we get a little interesting for the rest of the Authorization Profiles. These next group of Authorization Profiles are the Central Web Authentication / Hotspot Auth Profiles. They have a similar intent though they maybe configured differently. The intent is to catch the Guest Wireless Client’s Traffic and redirect them to a HTTP / HTTPS Splash Page where the guest can provide some sort of credentials to authenticate. Now in our deployment and blog series, we are going to use all three of the Guest Wireless options so we can show you how they work individually. The different Guest Options are listed below.
1. Self Registered Guest
2. Sponsored Guest
3. Hotspot Guest
The other thing to note here is that because we have two PSNs within our deployment, we want to make sure we can load balance our Guest Redirect and Authentication process between the two nodes. This is not normally an easy process to go through because of the session specific information. In our lab we do not have a Load Balancer so we are going to catch which ISE PSN Node actually received the clients guest information and then hard code that ISE PSN Node information in the redirect URL. All of this is shown in the next 6 Authorization Profiles as we are doing this for each Guest Method and each PSN Node.
For our Self Registration Guest Access Use Case, we are selecting Web Redirection, Central Web Auth. Then we are calling an Airespace ACL (do not use the Airespace Attribute separately here, you will want to use the field under the Web Redirection setting that just says “ACL”) named WLAN-CWA-REDIRECT. Now for all 6 of these Authorization Profiles we will actually be using the same redirect ACL on the WLC, but our other Authorization Profiles settings will be different. Next we have to select the portal we want to display for that redirected session, in this case we are using the Built In Self registered Guest Portal. Finally, and potentially the key option here is that we must hardcode the server FQDN so that the client session is sent to the correct ISE PSN, in this case we are doing ISE03.ZSIGA.LAB. This can all be shown in the below screenshots.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
9. WLAN-SELF-REG-CWA-ISE04
This Authorization Profile is the same as Number 8 above except that we are hard coding ISE04 in the URL given back to the client session. This is shown in the screenshots below.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
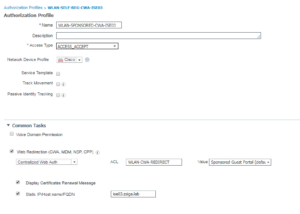
10. WLAN-SPONSORED-CWA-ISE03
For the next two Authorization Profiles, 10 and 11, they follow the same thought processes as Authorization Profiles 8 and 9 but use a different portal. Instead of using the Self Registration Portal, we are using the Sponsored portal for 10 and 11. Everything else is identical respectively to the ISE PSN and CWA information.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
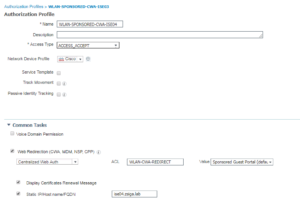
11. WLAN-SPONSORED-CWA-ISE04
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
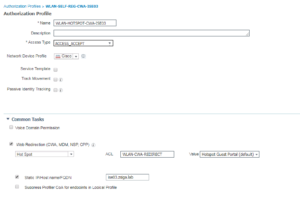
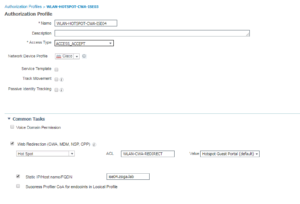
12. WLAN-HOTSPOT-CWA-ISE03
And Finally we have our Hotspot use case which is going to be configured pretty much the same as our Self Registered and Sponsored Guest Use Cases, just with a different splash page. To find the Hotspot option, we actually have to change our Web Redirection Method from CWA to Hotspot. Once we do that, we then can see the Hotspot Portals that are already configured. This is show in the below Screenshots for this Authorization Profile and # 13 as well.
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
13. WLAN-HOTSPOT-CWA-ISE04
Here is the Wireless Authorization Profiles Configurations:
Here is the Wireless Authorization Profiles Radius Attributes:
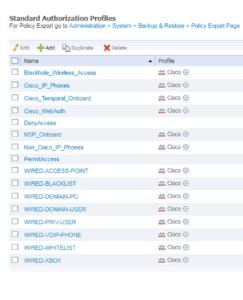
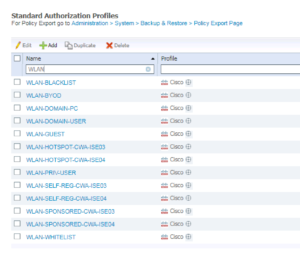
Wireless Authorization Profiles – Summary
Thats all of our Wireless Authorization Profiles for this deployment currently. Below is a screenshot of them all created! Next up is configuring our WLAN Policy Set!! 🙂 I can’t wait!
Related Resources:
Mentoring and Coaching with Zig:
Through your participation in a healthy mentoring and coaching relationship, you will benefit greatly from the education, the experiences, the influences, leadership and even the resources provided. Learn how you can accomplish more, in one year, than you could accomplish in your career…in your business…and in your life.
Accomplish More Now!!
Ask Zig:
Ask Zig episodes feature answers to the questions that you provide. Yes You! The questions can be technical, business, certification, or personal related. I can help out in all of these areas and much more. If you would like your question spotlighted and answered on the next #AskZig episode submit them now!
Submit Your #AskZig Question Now!!
Provide Feedback
- You can leave a comment on the blog!
- You can leave a voicemail at (617) 913-4103
- You can email us at Feedback@zigbits.tech
Engage with Zigbits further:
- Subscribe to the podcast on an iPhone or on an Android
- Follow Zigbits on Twitter!
- Follow Zigbits on LinkedIn!
- Follow Zigbits on Facebook!
Engage with me further:
Transparency:
This post may contain affiliate links to products or services were I may receive a level of compensation from your actions by following those links. This is seamless to you and does not add any additional cost to the products or services in question. In addition, I do not let any affiliate relationship cloud my judgement or my recommendation of a product or service. My recommendations will always be above reproach. This is my commitment to you Ziglets!




Hello,
Really interesting series. You explain it in great detail with supporting screenshots. Love it. I’m excited for the next chapter.
Sincerely,
Michaël
Hey Michaël,
Thanks for the feedback, really appreciate it! The next installment will be coming soon (within the next month), had some issues with my home lab over the last month or so. I just recently got it fixed so there should be a ramp up of installments for this Blog series!
R/S
Zig Zsiga